Fact: You Can’t Protect What You Can’t See
You’ve carefully planned your network security architecture and purchased the latest, most advanced security tools. But it’s not enough.
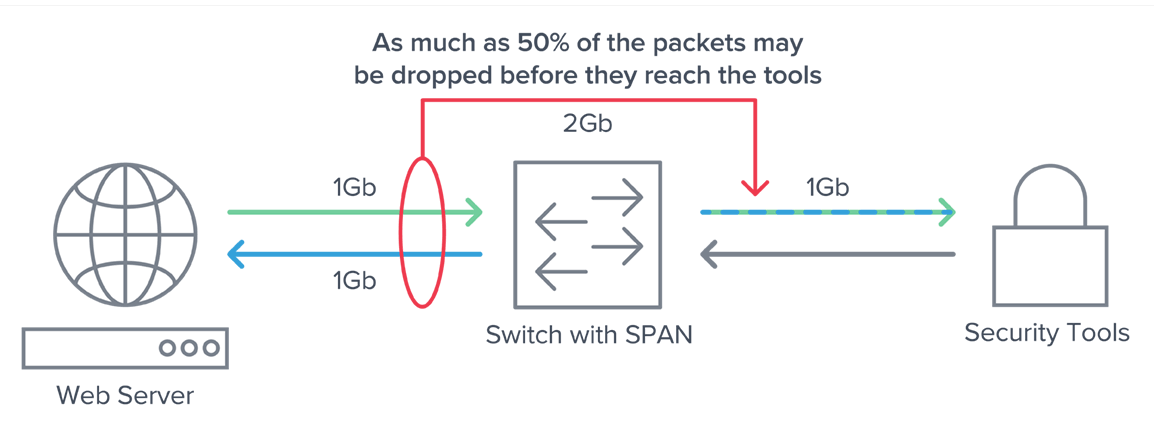
- Up to 50 percent of traffic never reaches your security tools because of dropped packets or blind spots.
- “Living off the land” (LoTL) attacks and malware can hide inside encrypted TLS/SSL traffic
- Attackers now use port spoofing to elude perimeter detection.
Achieving zero trust security requires seeing all traffic across your network—physical, cloud, and containers. You also need to know what the threats are, and how best to respond. The Gigamon Deep Observability Pipeline is the one platform for deep and pervasive visibility across your entire network.
Deep Observability Detects Threats Faster
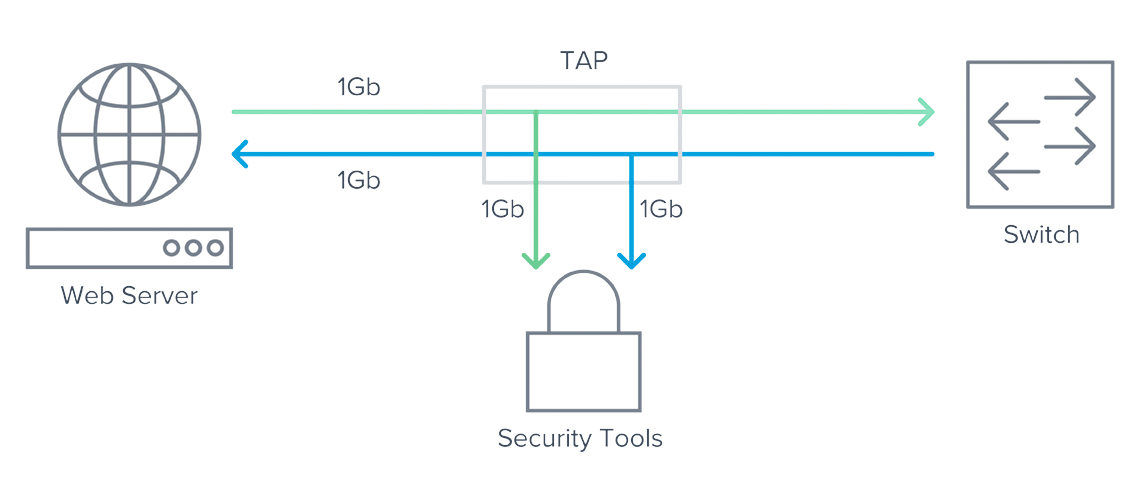
How you supply network traffic to your security tools is critical. If you rely on switch or router generated NetFlow or SPAN ports, your security tools are not getting everything they need for reliable analysis. A better way to collect and send traffic to your tools is by using network taps together with Gigamon, which sits between your tools and the network layer.
Gigamon gives you:
- Reliable, full-fidelity data: No more sample-based data or dropped packets due to overloaded equipment
- Cloud observability: Monitor VM and container traffic in private or private clouds
- Greater tool efficiency: Send only selected traffic to cloud-based tools or on-prem security stack
Get Encrypted Traffic Visibility
Cybercriminals use encryption to conceal threat activities like LoTL attacks, malware, and exfiltration attempts. You need a way to efficiently inspect encrypted east-west and north-south traffic and share it with tools.
Gigamon offers two solutions that eliminate blind spots created by encrypted traffic and takes the burden off expensive security tools.
- Gigamon Precryption™ technology provides visibility to all TLS encrypted (including TLS 1.3) cloud and container traffic.
- GigaSMART® TLS/SSL Decryption supports both inline and out-of-band decryption for legacy and modern encryption standards.
See Into Apps and Threats
To accurately detect threats and mitigate shadow IT, you need full application visibility plus network-derived intelligence. Gigamon Application Intelligence gives you the power to automatically identify applications and then send the right traffic to the right tools, so you don’t waste expensive security resources. Next, Gigamon provides your security and observability tools with valuable context around protocols and applications, helping you shorten investigative cycle times.
- Application Filtering Intelligence sends only relevant application traffic to security tools while filtering out the rest; use existing investments to secure East-West traffic.
- Application Visualization accurately identifies more than 3,500 applications using deep packet inspection so shadow IT activities and port spoofing attempts don’t pass unnoticed.
- Application Metadata Intelligence provides more than 7,000 metadata attributes, giving your SIEM, NDR, observability, and other security tools an unfair advantage over attackers.
Resources
Gigamon Deep Observability Pipeline
The Trouble with Visibility Into Cloud Traffic
Frost & Sullivan

"A couple of incidents that we had within the last six months we were able to catch quite quickly—within about an hour or so of the time the attacker took ownership of a server. We were able to catch them just in time before any real damage was done. And the reason is we have security tools in place, and Gigamon is feeding all the data into those security tools."

“Now we know everything that’s happening on our on-premises network as opposed to only 20 percent of it. The visibility adds a lot of value. We can have everything going to a single point without having multiple tap [test access point] devices all over the place.”
"With Gigamon, PT KAI has gained deep observability into risk and threat telemetry, and seamlessly integrated with our security tools, enabling informed decision-making and improved compliance."
“Gigamon [has] helped us move beyond playing whack-a-mole and chasing every vulnerability, toward a more strategic approach to cybersecurity. It gives us the data we need to build network resilience, reduce our attack surface, and make it harder for threat actors to impact our environment.”