Remove the Single Point of Failure from Your Network
How can you maximize the efficacy of inline threat prevention tools without compromising network performance or overcomplicating your security stack? The answer is simple: use a network bypass switch.
What is a Network Bypass Switch?
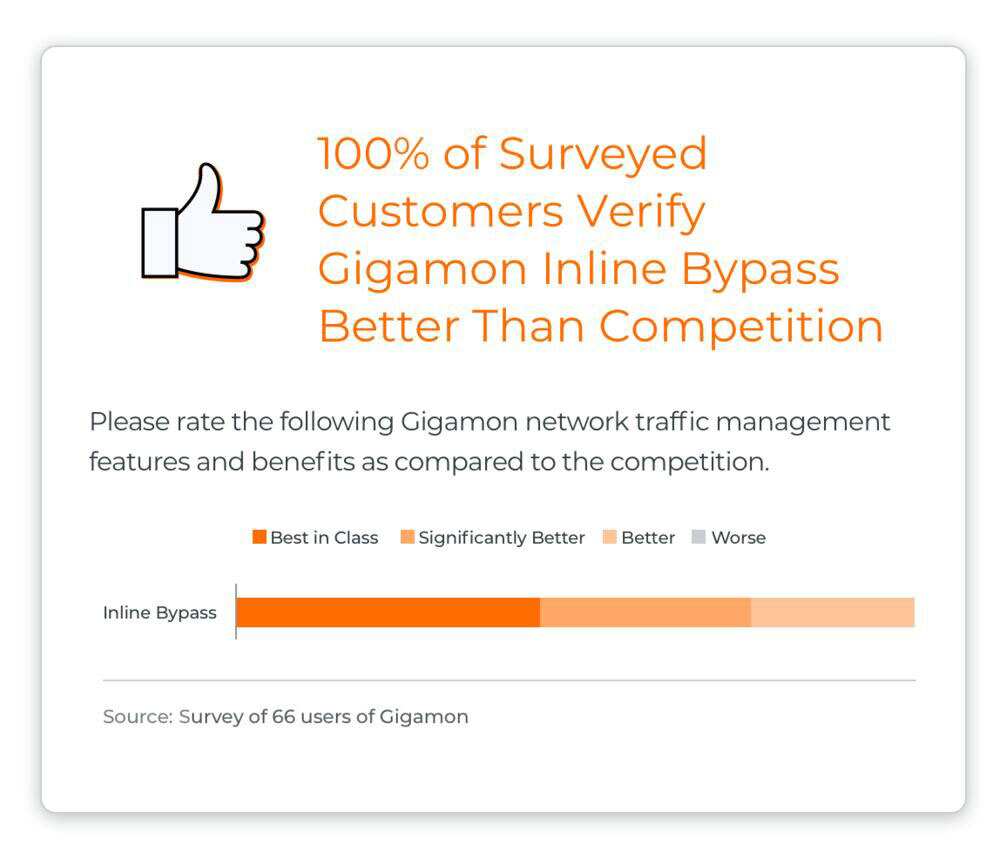
One way to maintain network performance and security is to deploy an external bypass switch, in the form of a Gigamon Inline Bypass Threat Prevention solution. An external network bypass switch (sometimes also called a Bypass TAP switch) is a device that acts as a fail-safe access network port for inline security tools, such as web application firewall (WAF), intrusion prevention system (IPS), and advanced threat protection (APT) solutions.
The bypass switch sends regular pulses to the in-line security appliance, which returns the pulses to the bypass switch, indicating that the security appliance is functioning. However, if the pulse is not returned to the bypass switch (indicating that the in-line security appliance is not functioning), the bypass switch automatically bypasses the appliance, ensuring that packets continue flowing optimally even during times of high traffic.
The Gigamon Deep Observability Pipeline offers an advanced inline bypass switch solution. This bypass switch enables enterprises to:
- Keep up with growing network traffic volumes by improving the performance of inline security tools.
- Streamline operations so you can complete security functions in hours versus weeks.
- Eliminate single points of tool failure by creating multiple resiliency layers.
- Solve the problem of asymmetric routing by enabling resilient (dual path) network architectures.
Most Advanced Physical Bypass Switch and Logical Bypass Switch
Inline bypass switch protection comes in two forms: logical and physical. Both bypass switch options operate on the principle that traffic must continue, even if you don't have the power to inspect it.
A physical electrical bypass switch provides users with the ability to physically forward packets in the event of a Gigamon visibility node power failure. This bypass switch also allows you to perform maintenance and upgrade your tools without impacting network operation or downtime. Switching to protected mode occurs automatically and without software intervention upon the loss of power.
Logical bypass happens in the event of inline tool failure and forwards traffic either to other tools or to the network. The bypass-switch system detects failure when the link with that tool breaks down, the inline tool stops responding or during loss of software control, thus enabling you to safely remove or upgrade an inline appliance, or even move it from one network segment to another, without disrupting the network.
GigaVUE-OS
Gigamon Resilient Inline Protection (GRIP)
See What Omdia Says About Precryption™

TRAINING
How Inline Bypass Fuels Inline Prevention
Get the most out of your visibility and security investments with free online learning.
“The performance of [Gigamon] has been exceptional. I don’t even know where the ceiling is because we haven’t even come close to hitting it. Everything that we’ve wanted to do with the company’s solution, we’ve been able to do.”
Have Questions?
We're here to help you find the right solution for your business.
By submitting this form, you agree to our Terms & Agreement. View our Privacy Statement.








