Network TAP and SPAN technologies both provide direct access to the actual packets navigating across networks, but which is the preferred methodology?
Accessing data in motion down to the packet level is the first step to acquiring network visibility, as nothing else provides a similar level of depth and granularity. The two most common methods to extract this information are SPAN and network TAP port technologies. But when it comes to TAP vs. SPAN ports, how do you decide which to use for a given situation?
Basic TAP and SPAN Technologies
A network TAP (Test Access Point)is a simple device that connects directly to the cabling infrastructure. Instead of two switches or routers connecting directly to each other, the network TAP sits between the two devices and all data flows through the TAP. Using an internal splitter, the TAP creates a copy of the data for monitoring while the original data continues unimpeded through the network
As seen in Figure 1, data from a network is transmitted (Tx) from device A to be received (Rx) by device B. At the same time, data can travel in the reverse direction where device B transmits data to device A. Most TAPs separately copy the transmit signals from A and B and send them to separate monitoring ports (TxA and TxB).
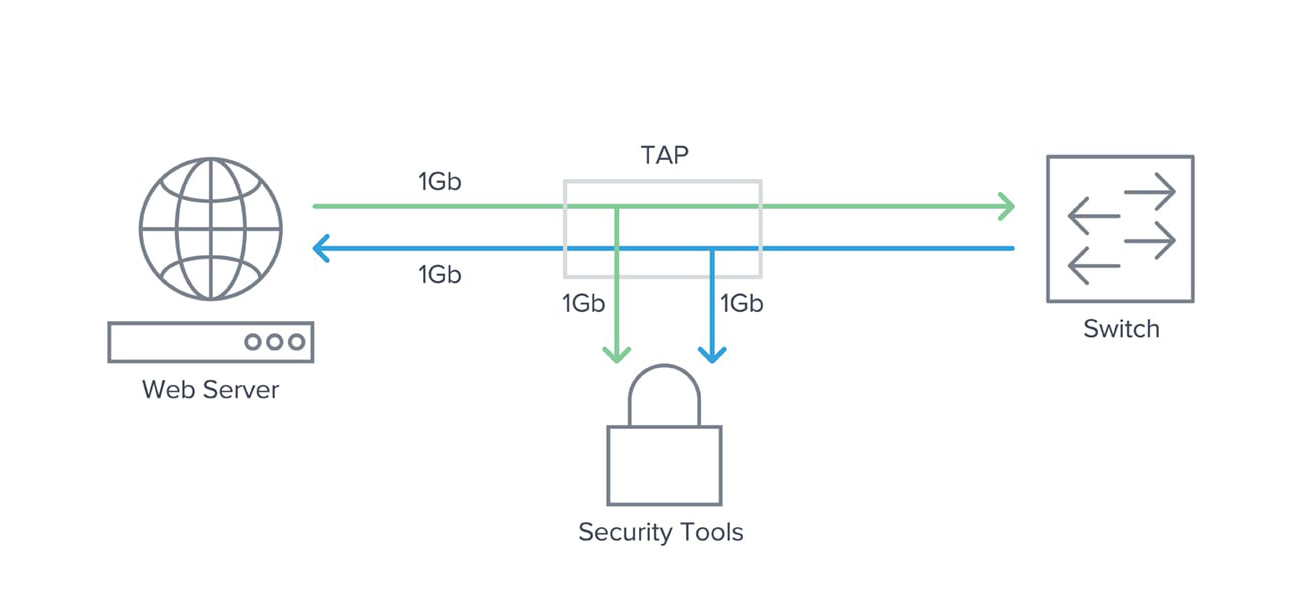 Figure 1: TAP flow diagram
Figure 1: TAP flow diagram
This technique ensures every packet of any size will be copied and eliminates any chance of oversubscription. Once the data is tapped, the duplicate copy can be used for any sort of monitoring, security or analysis.
Note that inserting a TAP into an existing network link requires a brief cable disconnect, so TAPs are typically installed during a maintenance window.
SPANs
A SPAN port (sometimes called a mirror port) is a software feature built into a switch or router that creates a copy of selected packets passing through the device and sends them to a designated SPAN port. Using software, the administrator can easily configure or change what data is to be monitored. Since the primary purpose of a switch or router is to forward production packets, SPAN data is given a lower priority on the device. The SPAN also uses a single egress port to aggregate multiple links, so it is easily oversubscribed.
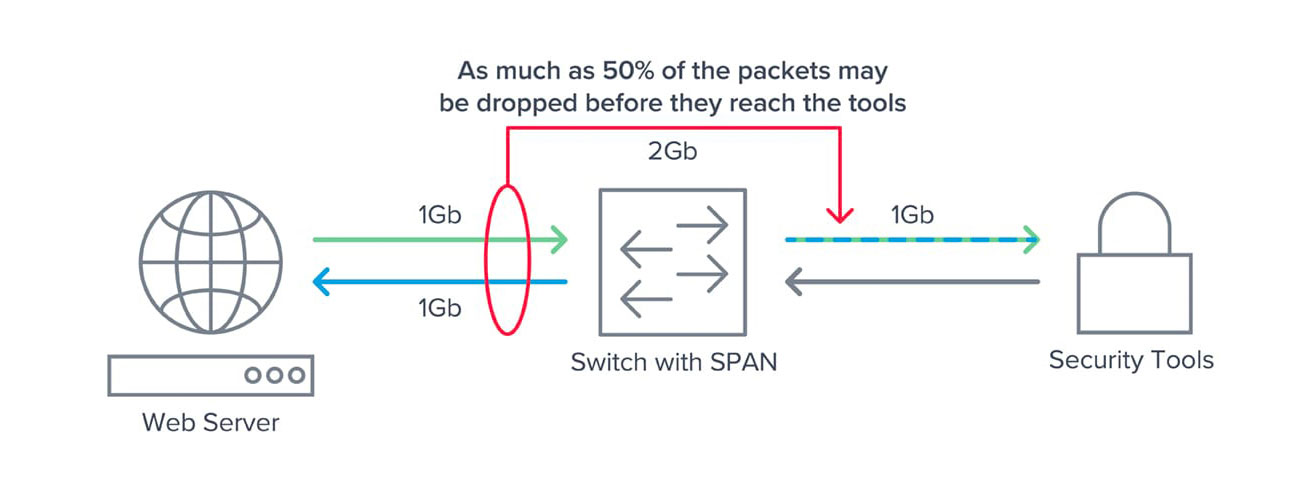 Figure 2: Why SPAN ports are easily oversubscribed
Figure 2: Why SPAN ports are easily oversubscribed
Both situations can lead to dropped packets. SPANs work best for ad hoc monitoring of low volumes of data in locations where TAPs have not been installed. SPANs still represent the only means for accessing some types of data, such as data crossing port-to-port on the same switch.
TAP vs. SPAN: Why Network TAPs Are Preferred Over SPAN Ports
In today’s modern, high-speed networks, network TAPs are the recommended choice. Here’s why:
- TAPs create an exact copy of the bi-directional network traffic at full line rate, providing full fidelity for network monitoring, analytics and security.
- Passive TAPs provide continuous access to traffic and require no user intervention or configuration once installed — a true set-and-forget solution.
- SPAN ports are easily oversubscribed, resulting in dropped packets and leading to unsatisfactory or inconsistent results for monitoring and security purposes.
- SPAN traffic has the lowest priority when it comes to forwarding and may not achieve full line rate. In some situations, low priority can cause packet drop even on a SPAN port operating at single-digit utilization.
- The SPAN application can have a negative performance impact on the switch itself, sometimes affecting network traffic.
- Because SPAN traffic is easily reconfigured, SPAN output can change from day to day or hour to hour — resulting in inconsistent reporting.
- Legal regulations or corporate compliance sometimes mandate that all traffic for a particular segment be monitored. This can only be guaranteed with a TAP.
- Incorrectly configured SPAN ports have been known to impact network performance or even cause network outages.
- SPAN ports are limited in number compared to the number of ports that may require monitoring, and they consume ports that could otherwise be carrying production traffic.
- TAPs don’t care what protocol is carried in the traffic or if it is IPv4 or IPv6. All traffic is passed through a passive TAP, including packets with errors. Active TAPs typically block errors but forward everything else.
The bottom line is TAPs should be used wherever 100 percent visibility and traffic fidelity is required. Anytime traffic volumes are moderate to high, deploy network TAPs. As a best practice, install TAPs during the early design phase and pass the traffic directly to a Gigamon visibility node. Even if the traffic is not yet required for daily inspection, it will be available for ad hoc troubleshooting or security inspection within seconds and without needing to involve change management.
When to Use SPAN Ports
There are situations where a TAP is not practical. Consider using SPAN ports for the following exceptions:
- Limited ad hoc monitoring in locations with SPAN capabilities where a network TAP does not currently exist.
- Locations with limited light budgets where the split ratio of a TAP may consume too much light. (Another possibility here would be to use an active TAP or more powerful optics capable of longer distances.)
- Production emergencies where there is no maintenance window in which to install a TAP.
- Remote locations with modest traffic that cannot justify a full-time TAP on the link.
- Access to traffic that either stays within a switch or never reaches a physical link where the traffic can be tapped.
- As a low-cost troubleshooting alternative where links have low utilization.
In summary, both network TAPs and SPAN ports can provide valid access to data if properly positioned.
So TAP where you can, and SPAN where you must.
Next Step: Monitoring, Managing, Securing
TAP and/or SPAN are just the first step in the process of achieving pervasive visibility across your entire network infrastructure. Once traffic has been captured over either TAPs or SPAN ports, you can send it to the Gigamon Deep Observability Pipeline to be monitored, managed and secured. GigaSMART® applications are also available to optimize traffic and deliver relevant data to the specific tools you rely upon to improve their performance and efficiency.
For more information or to download the full PDF, please click here.







