Gigamon Deep Observability Pipeline
Supercharge your security and observability tools with network-derived intelligence to eliminate blind spots and reduce tool costs.
CLOUD VISIBILITY
DATA CENTER VISIBILITY
NETWORK SECURITY
TRAFFIC INTELLIGENCE
A NEW AI ERA BEGINS
AI builds on deep observability to enhance traffic intelligence, threat detection, and governance across the hybrid cloud.
DATA CENTER VISIBILITY
A Thriving Partner Ecosystem
Gigamon reseller and integration partners design, implement and optimize best-of-breed and validated joint solutions.
FIND A PARTNER
NOT A PARTNER?
ALREADY A PARTNER?
Proven Support and Services
Our global support team is committed to creating experiences of unmatched quality, scalability and efficiency.
OVERVIEW
GET SUPPORT
ASK THE COMMUNITY
voice of the customer
Gigamon serves the most security conscious government agencies and businesses around the world, enabling them to gain deep observability they require to better secure and manage hybrid cloud infrastructure.
CUSTOMERS
Resource Library
Your one-stop hub to explore content resources and stay current on the latest in how to amplify the power of your cloud, security and observability tools.
WHY GIGAMON
We offer a deep observability pipeline that efficiently delivers network-derived intelligence to cloud, security, and observability tools to eliminate blind spots, optimize traffic, and reduce tool costs, enabling you to better secure and manage hybrid cloud infrastructure.
Popular Content
Optimize application performance and troubleshooting.
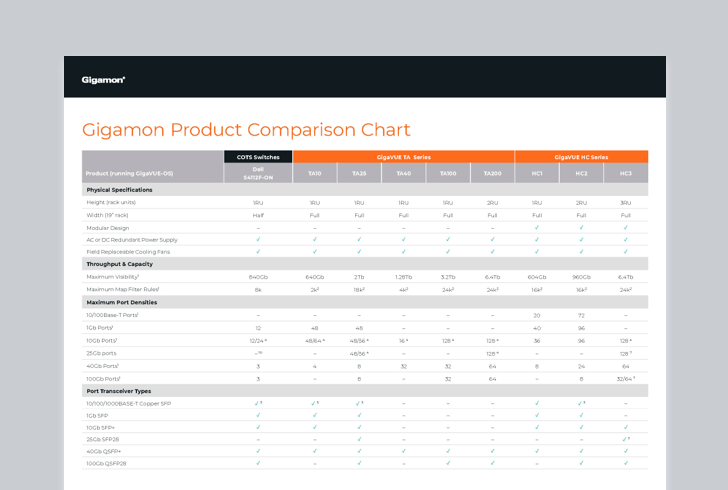
Check out our detailed GigaVUE product comparison chart.
Not seeing what you're looking for? Ask our community of Gigamon users and experts.