Zero Trust is an approach to cybersecurity, not a product or even a specific architecture. The core principle of this approach is not to trust any user or asset on your network and work on the assumption that “an enterprise-owned environment is no different — or no more trustworthy — than any non-enterprise-owned environment” (from the 2020 NIST Special Publication 800-207 “Zero Trust Architecture”).
The concept of Zero Trust carries significant implications. Philosophically, it shifts from assuming trust in employees and assets to treating none as inherently trustworthy. Continuous evaluation and verification of trust on a transactional basis become vital, ensuring only authorized entities access data and assets. Organizations must transform their architecture, culture, and cybersecurity mindset. Network-wise, the defensive perimeter relocates from network edges to internal assets. Yet, many maintain perimeter defenses while bolstering security with internal controls, like network and host-based measures, close to data. This "defense in depth" principle, though not new, remains crucial for transitioning to a Zero Trust security approach.
Zero Trust Is a Journey
Zero Trust is a journey, not a destination. The journey consists of both technical and cultural shifts, oftentimes enforced by executive mandate. While cultural aspects are harder to implement, they’re crucial for success as it’s now widely accepted that user training, behavior, and buy-in are critical to Zero Trust's success. There are now several roadmaps or models that have been developed for Zero Trust by standard bodies and technology vendors. Figure 1 illustrates a typical representation of a Zero Trust model.
One of the key things these models have in common is the need for visibility. This is shown as one of the foundation layers in this model. Visibility is critical to Zero Trust because, to close this section with another cliché, you can’t protect what you can’t see. This is why visibility and analytics are built in as one of the foundational layers of the CISA Zero Trust model.
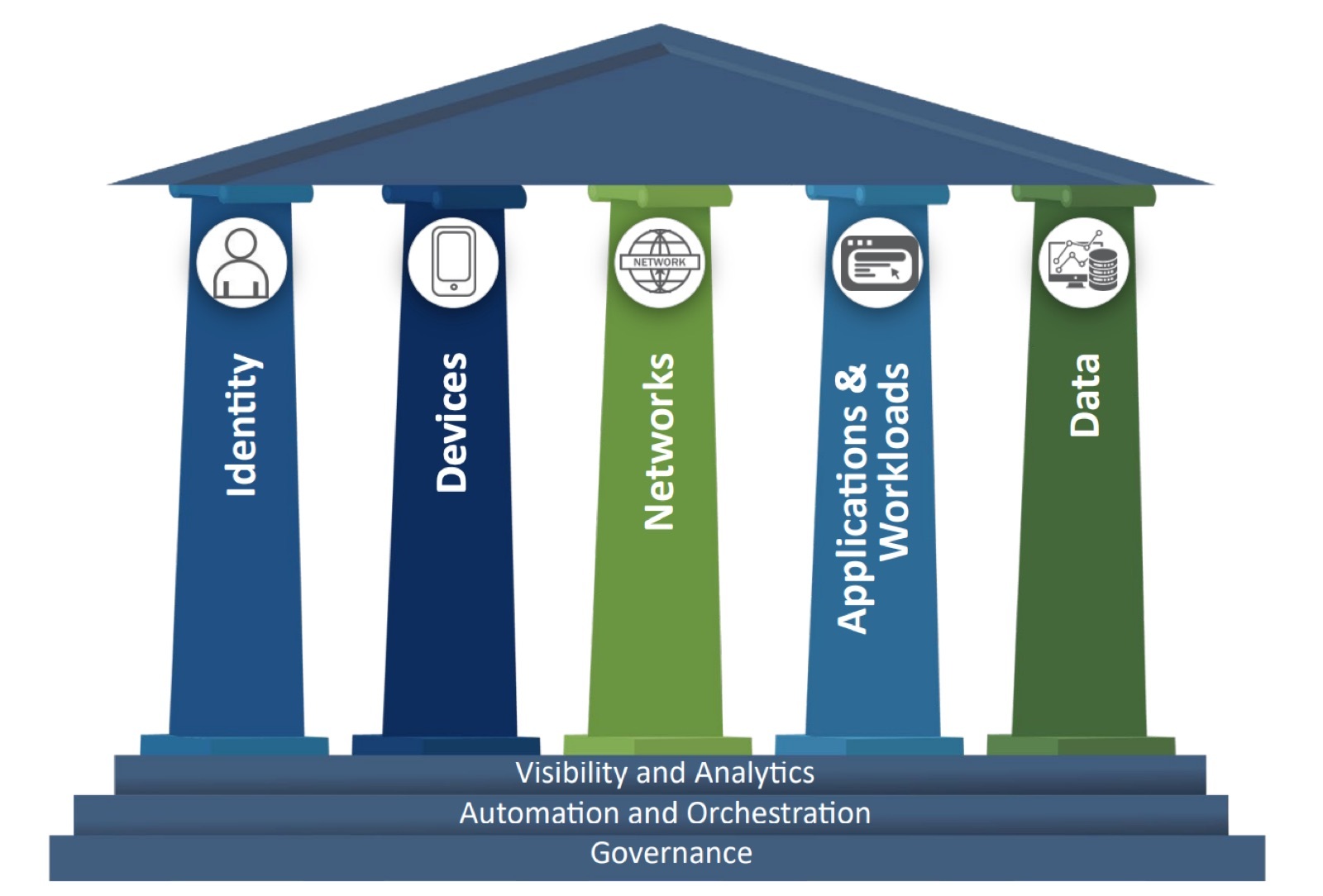
Figure 1. CISA Zero Trust Model as defined in the April 2023 Cybersecurity and Infrastructure Security Agency publication Zero Trust Maturity Model.
Visibility Enables the Three Key Principles of Zero Trust
Although Zero Trust models often show multiple pillars and foundational layers, at its core, Zero Trust is based on three key principles: Adopt a breach mentality, never trust, and continuously verify. These principles assume that organizations have full visibility of all the hardware and software assets, applications and data assets, users, and devices on their networks. This visibility enables these Zero Trust principles to be effectively implemented.
Adopt a Breach Mentality
With the rising sophistication of cyberattacks, organizations adopting a Zero Trust architecture must operate under the assumption of repeated breaches. Swift and accurate breach identification is crucial. Further, the architecture should have controls, such as segmentation, that can limit the impact of these attacks, often called “the blast radius.” This is achieved by developing a defense-in-depth security posture at all levels of the network.
Never Trust
This is the most easily understood of the Zero Trust principles but one of the hardest to put into practice since most systems within an organization have been traditionally built around an implicit trust model that assumed the trustworthiness of users, devices, and controls.
Despite the conflict between the Zero Trust philosophy of complete distrust and the trust culture nurtured by organizations over decades, it’s imperative to keep Zero Trust. Evidence indicates that a substantial number (of over 40 percent) of breaches are caused by employees or contractors acting in bad faith or human error.
Continuously Verify
The traditional trust model assumes stability, disregarding inevitable changes in behavior and technology. Zero Trust counters this by requiring constant verification of all network entities against defined security policies. For example, attackers get smarter, employees get careless, login credentials become compromised and so on. A key component of a Zero Trust network is a policy engine that has full visibility into all network activity and continuously verifies and enforces activities against these policies.
What Are the Benefits of a Zero Trust Architecture?
Some of the main benefits include:
- Meeting governmental mandates, regulations, or guidelines
- Reducing the cost of cyber insurance policies
- Reducing the perceived risk or exposure to GDPR or similar liabilities
- Standardizing security across disparate operating subsidiaries or divisions
- Measuring and mitigating business and technology risks
- Protecting brand reputation and trust
To achieve these benefits, 148 organizations surveyed in Q1 2023 identified the following Zero Trust use cases as their top priorities:
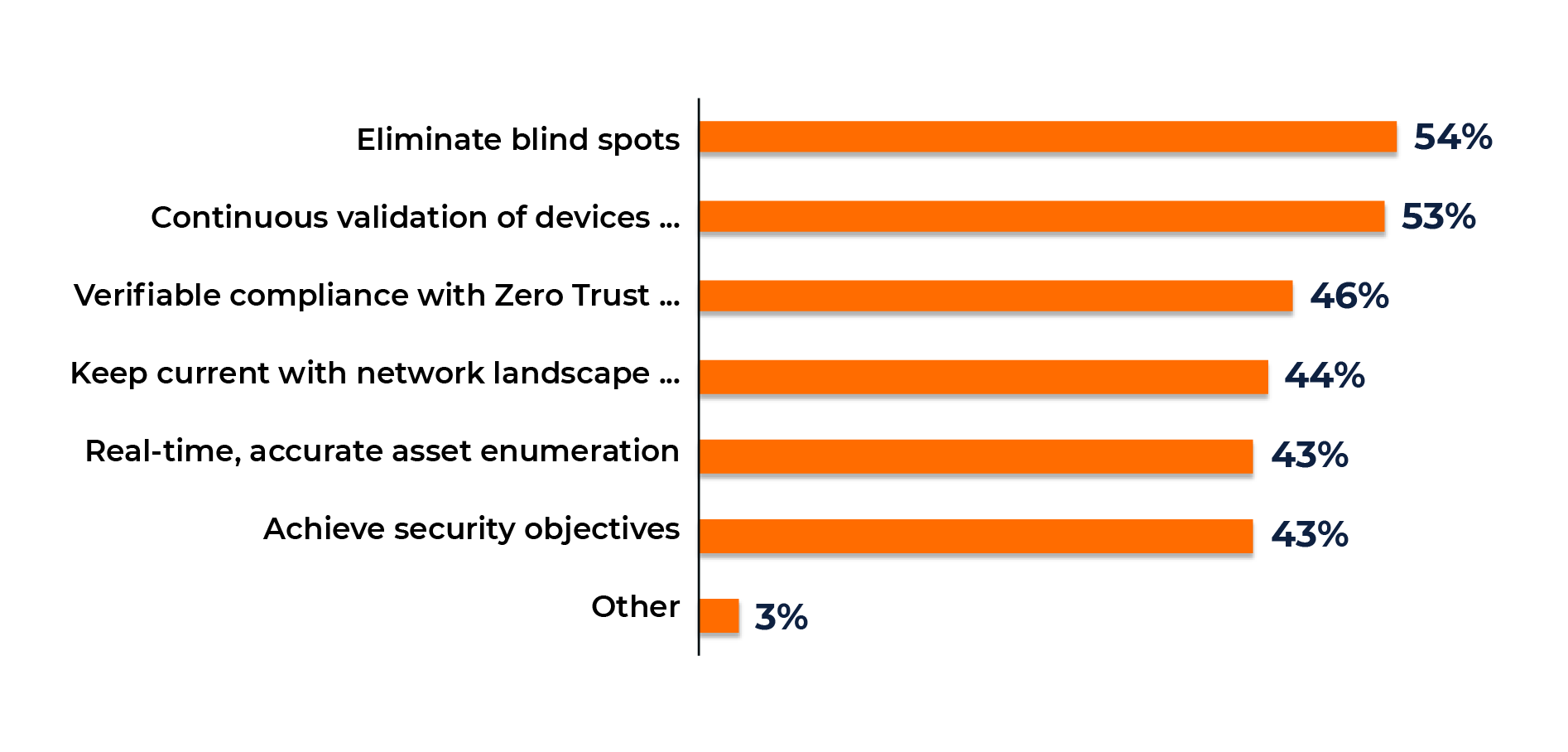
Figure 2. Results of the Pulse Survey “Approaches to Visibility in a Zero Trust” (2023), conducted by Gatepoint Research.
Whatever the expected benefits and priority use cases driving to a Zero Trust architecture, organizations must map out a clear and realistic strategy for their migration to Zero Trust. Gigamon, the industry leader in deep observability, has worked with thought-leader John Kindervag, formerly of Forrester Research and the man who originally coined the term “Zero Trust,” to develop a whitepaper that discusses:
- Why maintaining high-fidelity visibility is at the heart of a successful approach to Zero Trust
- How to eradicate blind spots and get true visibility
- The five steps to building a Zero Trust network
“Gaining complete visibility into the network is like lighting up the whole street. When it comes to implementing Zero Trust, this is the best place to start.”
Five Steps to Building a Zero Trust Network
Unless mandated by executive order or regulation, you should choose the ZTA model that best suits your organizational goals. One such model is that proposed by John Kindervag, who has defined the five steps necessary to build a Zero Trust network, which can be summarized as follows:
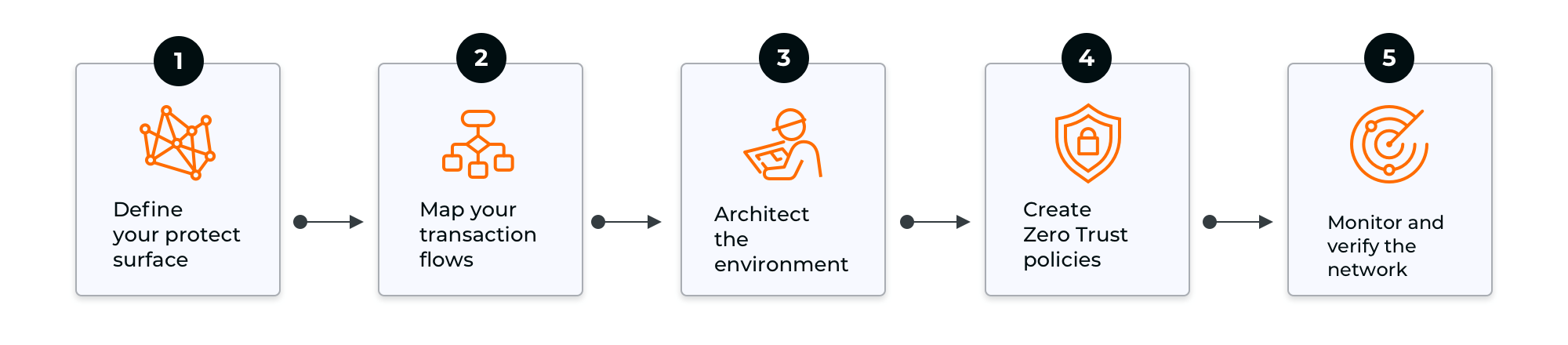
- Define your protect surface
Defining your protected surface means identifying the data, applications, assets, and services that are important to your organization. Define and prioritize what needs to be protected as part of your Zero Trust approach.
- Map your transaction flows
Define the transaction flows that link users, applications, and data. This will also help organizations understand where they need to place controls to protect and verify these critical flows of information.
- Architect the environment
Once an organization has defined the protect surface and transaction flow, it is relatively straightforward to architect a Zero Trust network and to determine, for example, where firewalls or other tools that segment the network need to be located. A guiding principle for the design of a Zero Trust network is that these controls should be placed as close as possible to the assets that are being protected.
- Create Zero Trust policies
Policies can be developed by answering basic questions such as: Who should have access to a resource? What applications should they be allowed to access? When and in what circumstances should access be allowed? How will we verify that these policies are being enforced? Each policy statement will come down to a simple “allow” or “deny,” but it may take massive amounts of data — and very complex criteria — to make that decision.
- Monitor and verify the network
The final step in the process is to determine how an organization will instrument the network and what telemetry needs to be captured to ensure that Zero Trust policies are being followed and that this can be independently verified. For example, if telemetry is based on log files, what controls are in place to ensure that logs have not been tampered with? As we identified earlier, modern networks are in constant flux, so this process must be based on continuously observing and verifying the behavior of all network assets.
How the Gigamon Deep Observability Pipeline Helps You Build a Zero Trust Architecture
The Gigamon Deep Observability Pipeline provides visibility into all data in motion on the network, and, as identified in this blog, this is critical for implementing and continuously verifying a Zero Trust network.
Gigamon has extensive experience working with our customers to implement Zero Trust networks, especially within the federal government.
To learn more about how Gigamon can help you build a Zero Trust network, visit the Zero Trust page of our website, or download the John Kindervag whitepaper.

“The Gigamon platform enables us to feed all the different tool sets we have acquired and offers us X-ray capability, not only in the physical world but also in the virtual world.”







