Efficiently Inspect and Monitor Encrypted Traffic
Encrypted traffic surge demands smarter decryption. The upcoming shift to Post-Quantum Cryptography (PQC) will introduce new encrypted data streams that can create blind spots for security tools. GigaSMART® TLS/SSL Decryption unlocks deep observability for security and monitoring tools, allowing you to protect your network against threats. Decrypt selectively, maintain data privacy, optimize performance, and validate against security policies for Zero Trust compliance.
TLS/SSL Decryption empowers SecOps, NetOps, and application teams to:
- Unmask hidden threats in encrypted traffic
- Decrypt once and feed many tools with centralized decryption
- Feed both inline and out-of-band tools
- Gain visibility into traffic that may be protected by PQC algorithms
- Simplify monitoring and troubleshooting
- Visualize encrypted traffic
Streamline and boost the effectiveness of your security and monitoring tools by delegating resource-intensive decryption tasks.
Benefits
Leverage Existing Tools
Allow inspection by security and monitoring tools while maintaining overall data and security posture.
Maintain Data Encryption
Enable decrypted data to be
re-encrypted before sending
it to its intended destination.
Reinforce Zero Trust
Validate encrypted traffic to reinforce Zero Trust architectures and enforce security policies.
See How it Works
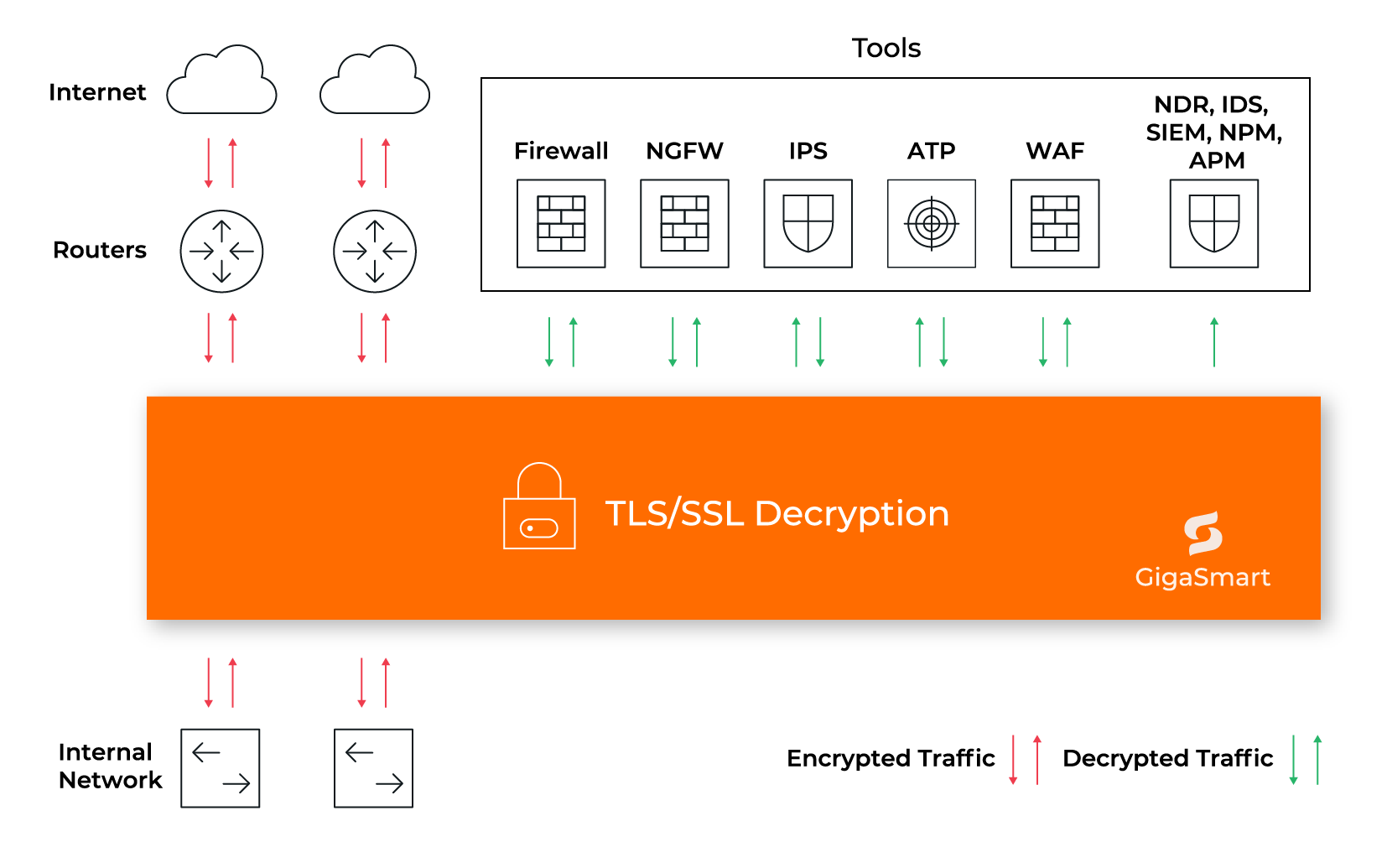
Product Details
GigaSMART centralizes decryption, including TLS 1.3, enhancing security and performance across the hybrid cloud. It exposes malware hidden in encrypted traffic and supports both inline and passive modes.
Flexible Deployment Options
Enable TLS/SSL detection on any port or application, from 10 Mb up to 100 Gb interface support. Decrypt once, feed as many tools in any sequence as required.
Integration Options
Integrate smoothly with the Venafi Trust Protection Platform, Thales Luna HSM, and Entrust nShield HSM to centralize key management and validation.
Future-Proof Scalability
Protect tool performance and scale as needed. Support easy tool maintenance, updates, and upgrades. Add or remove tools with no service interruption.
Rapid Troubleshooting
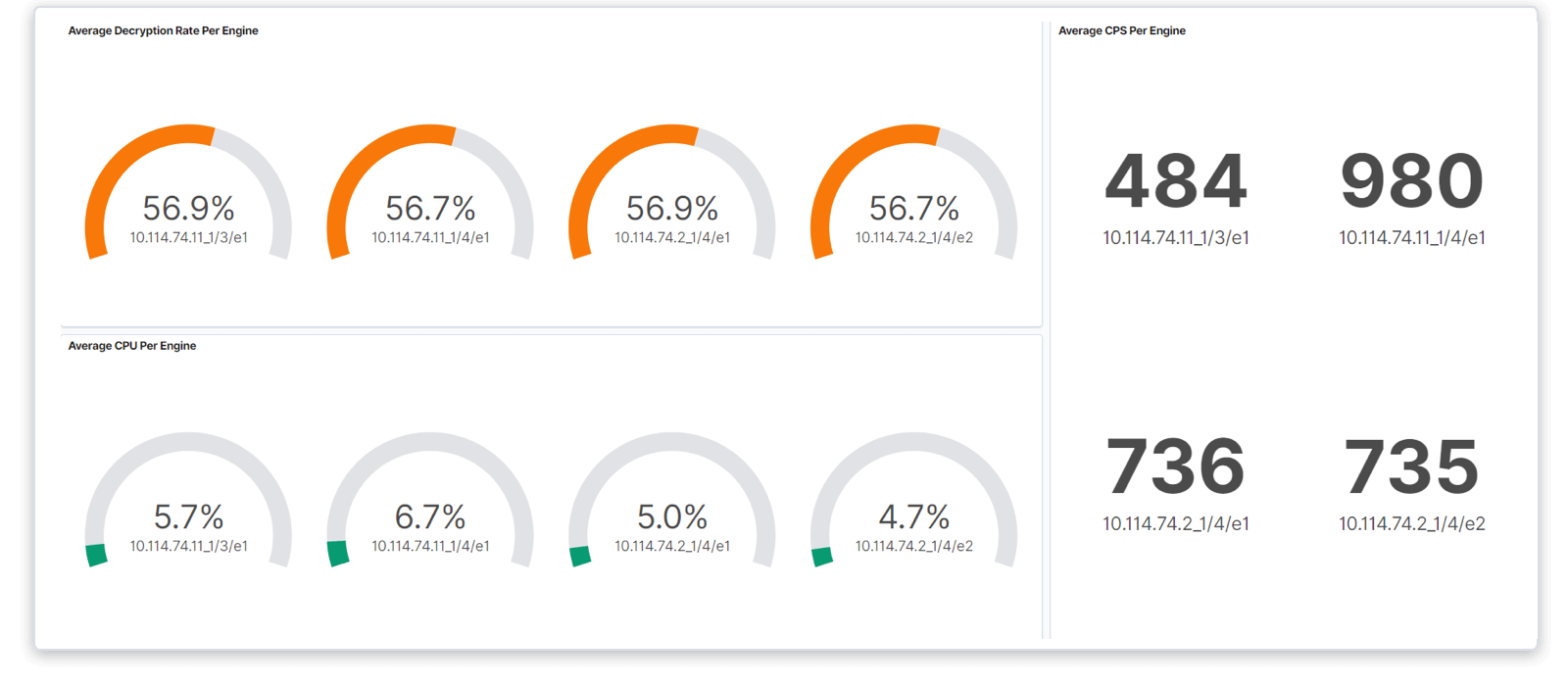
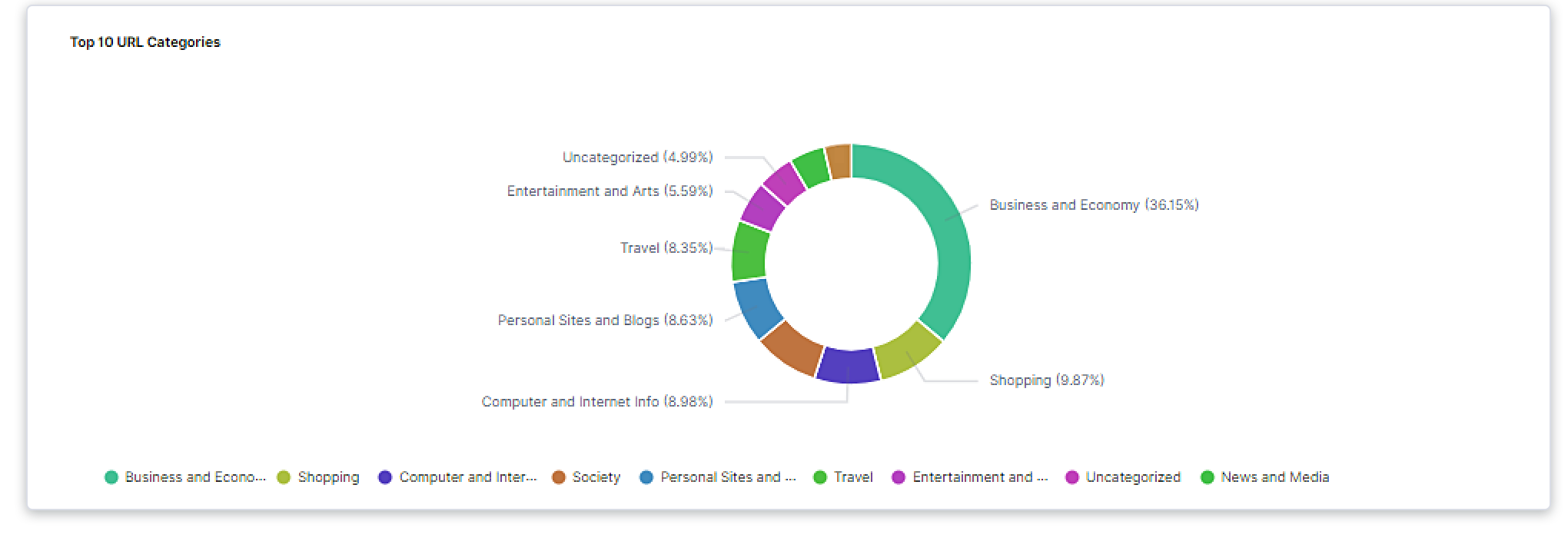
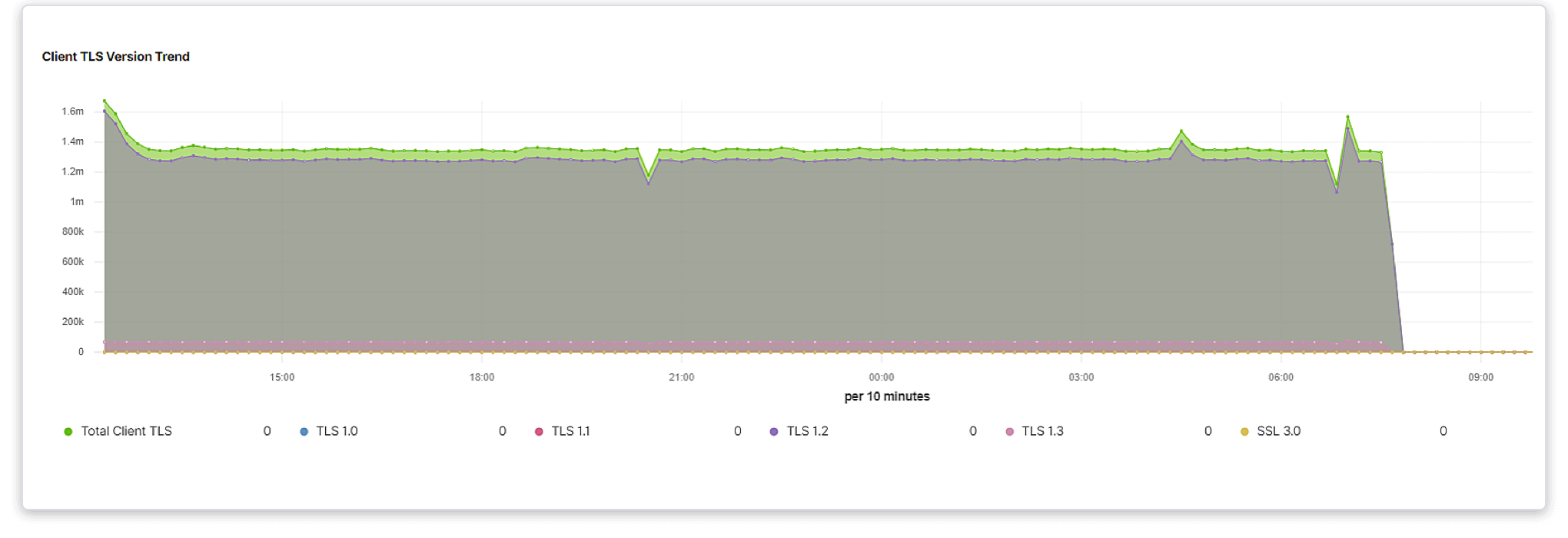
Assess performance, compliance, and risks with granular visualization controls in the TLS/SSL Dashboard.
With the TLS/SSL Dashboard, you can:
"The “harvest now, decrypt later” threat has made the transition to quantum-safe cryptography a global imperative. Because today’s public-key cryptography is fundamentally at risk, governments and regulatory bodies are pushing organizations to act now. This is not a strategic choice but a mandated requirement to ensure long-term data security."
Best Practices for Quantum Safe Networks, October 2025 - ID G00839731 By: Jorge Aragon, Matthew Brisse
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
“Before Gigamon, we had out-of-band SSL decryption everywhere, and we were decrypting about 65 percent of traffic on average. Now, with the GigaSMART SSL decryption engine, we typically get well over 90 percent visibility in the encrypted traffic.”
“Gigamon is traditionally thought of as a network efficiency platform, but the underlying technology has radical implications in cybersecurity as well. Visibility of encrypted packets is more of a must-have than a like-to-have, and intelligent traffic handling is a requisite in optimizing bandwidth and reducing storage costs.”
"It's a set it and forget it type of appliance, I love the deduplication features, SSL Decryption, and multiple cloud virtual tap functionality! So this is a very hybrid solution!"
Gartner® and Peer Insights™ are trademarks of Gartner, Inc. and/or its affiliates. All rights reserved. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.
Resources
GigaSMART TLS/SSL Decryption
Gigamon Analysis Exposes Risks of Encryption
See What Omdia Says About Precryption®

Dive Deeper
See what your peers are talking about in the VÜE Community
Watch quick demos showcasing real-world use cases from the Tech Hub
To explore more use case videos, visit the Tech Hub.
Frequently Asked Questions
Decryption is the process of breaking down encrypted data back into its original, comprehensible and readable form. It is typically performed in controlled environments. Usually, the objective behind decryption is to inspect the content of encrypted traffic and look for malicious activities, compliance checks, or troubleshooting. This process often requires access to private keys or the use of a trusted intermediary to decrypt and then re-encrypt the data before forwarding it to its destination.
SSL decryption is essential for cybersecurity because most internet traffic is encrypted using TLS. Although TLS has replaced SSL as the primary security protocol due to SSL’s security flaws, the term "SSL decryption" is still commonly used to refer to TLS decryption.
Decrypting encrypted traffic allows organizations to inspect data for threats, enforce security policies, and maintain compliance. The decryption processes for SSL and TLS are quite similar.
GigaSMART SSL/TLS decryption is one of the best examples of how decryption can be used to enhance network visibility to elevate the secure posture. Also, this is fundamental component for building a zero trust architecture.
When a client accesses your website, SSL/TLS decryption allows you to analyze the traffic sent through their browser. Since this traffic is encrypted as it moves across the web, decryption enables security and monitoring tools to inspect it before re-encrypting and forwarding it securely.
GigaSMART TLS/SSL decryption plays a key role in the Gigamon Deep Observability Pipeline. As traffic flows between applications and workloads within on-perm and hybrid cloud environments, it is frequently encrypted to safeguard sensitive data from unauthorized access.
When traffic moves between routers and your internal network, SSL/TLS decryption can enable you to send decrypted traffic to security and monitoring tools. All traffic is then re-encrypted again before being sent to its destination—whether that’s your internal network or the internet.
While TLS is the primary encryption protocol used today, GigaSMART supports both SSL and TLS decryption. This advanced capability provides full visibility into your network traffic—not just a list of encrypted packets.
Designed to seamlessly integrate with existing security and monitoring tools without compromising data integrity, GigaSMART plays a crucial role in building and maintaining a robust security posture and act as the foundation for a zero trust architecture.
The upcoming shift to Post-Quantum Cryptography will introduce new encrypted data streams that can create blind spots for security tools. Cryptographic technologies are integrated throughout enterprise networks, making it difficult for organizations to know where to start with PQC readiness. Gigamon helps Gigamon helps organizations discover and inventory cryptographic technologies within their infrastructure. Gigamon provides visibility into traffic that may be protected by PQC algorithms, ensuring security tools can still inspect it.
If you’d like to better understand how GigaSMART SSL/TLS decryption works and how it can benefit your network, you can book a free demo to learn more.
Our Tech Hub offers a collection of video demos showcasing our products in action. For deeper insight, check out our TLS decryption webinar to brush up on the fundamentals of SSL and TLS decryption.