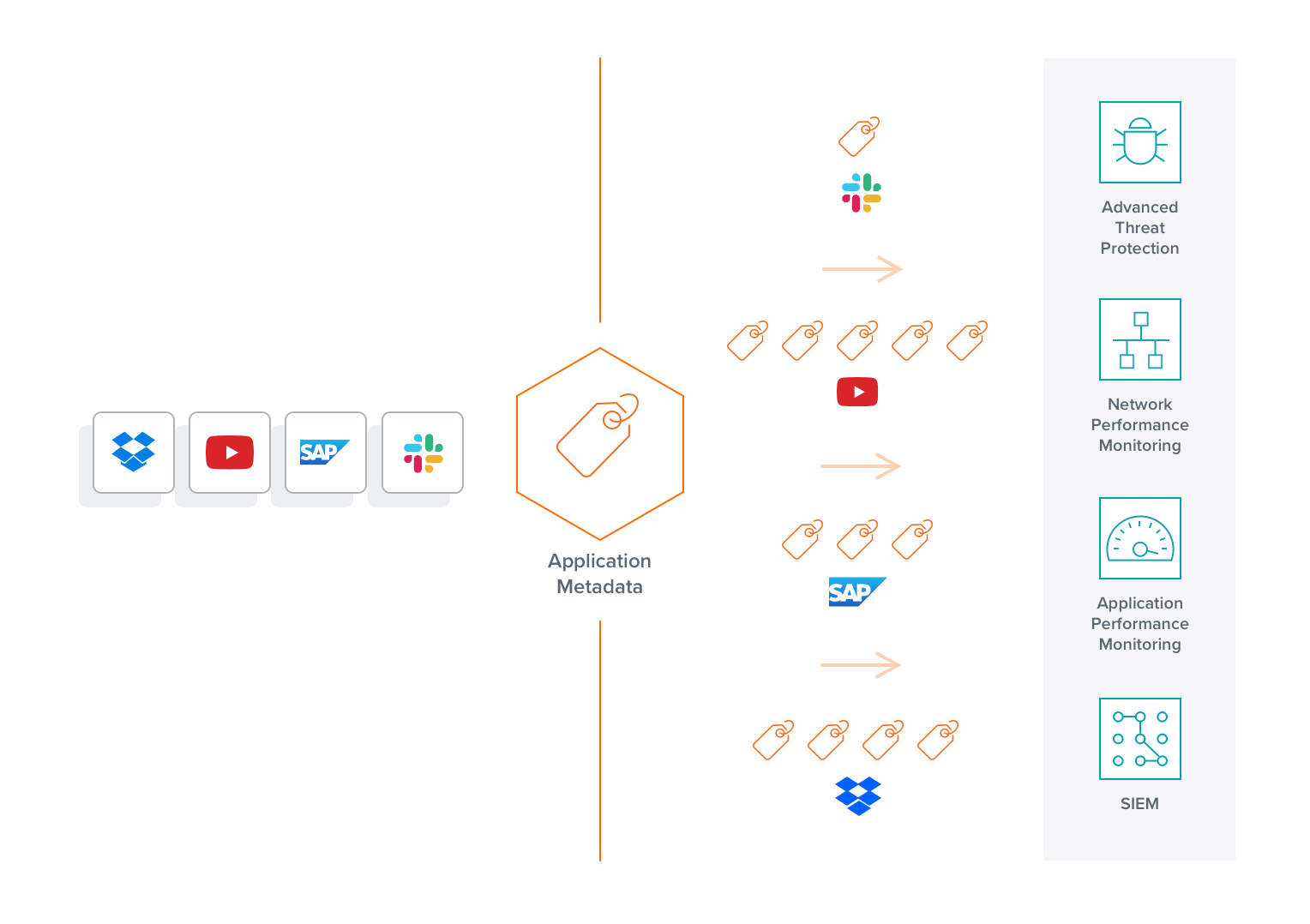
Deep Application Intelligence for Smarter Tools
Analytics tools are only as smart as the data they receive. Gigamon Application Metadata Intelligence, powered by Gigamon AI, empowers your Observability, Security Information and Event Management (SIEM), and Network Performance Monitoring tools with critical metadata attributes across thousands of businesses, consumer, and IT applications and services. Gain deep application visibility—including into GenAI applications—to quickly pinpoint performance bottlenecks, quality issues, and potential network security risks.
As part of Gigamon Application Intelligence, Application Metadata Intelligence (AMI) helps you effectively monitor and manage complex digital applications to support your digital transformation initiatives.
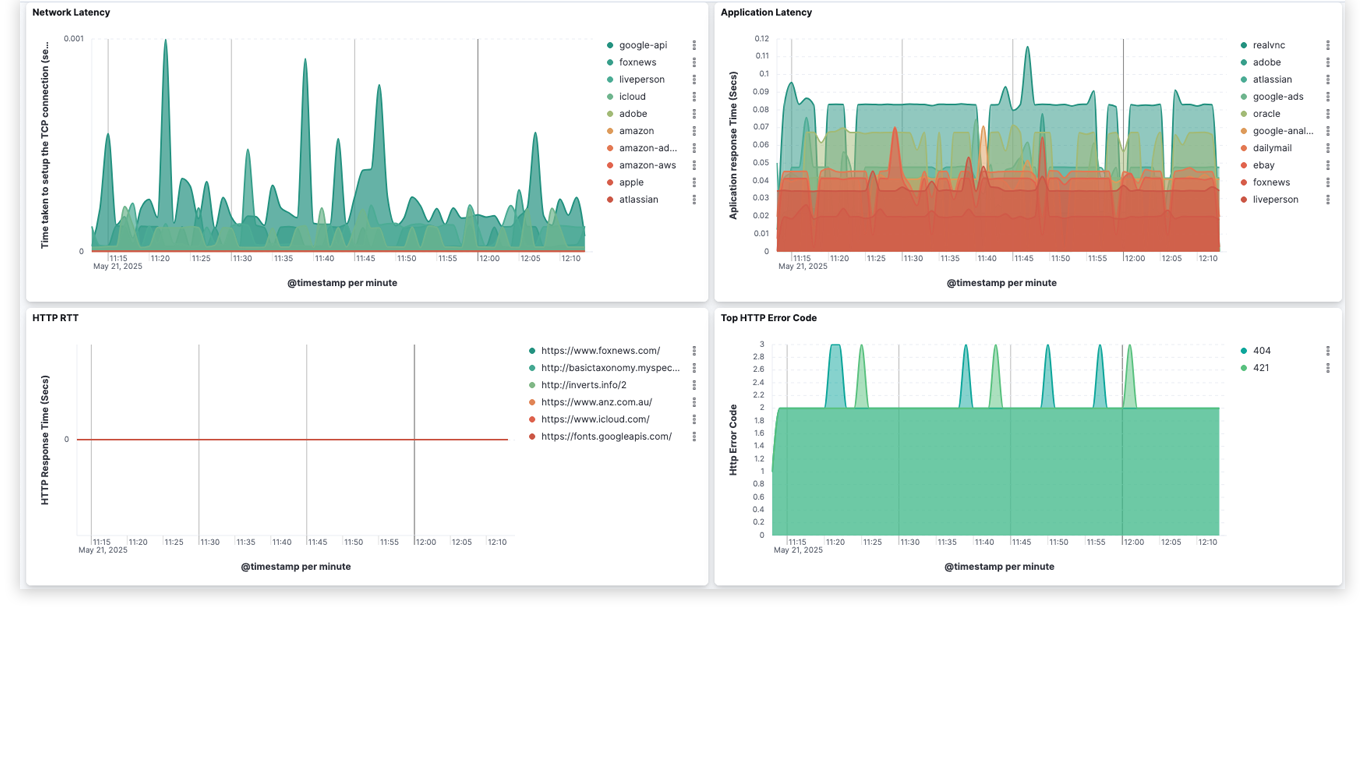
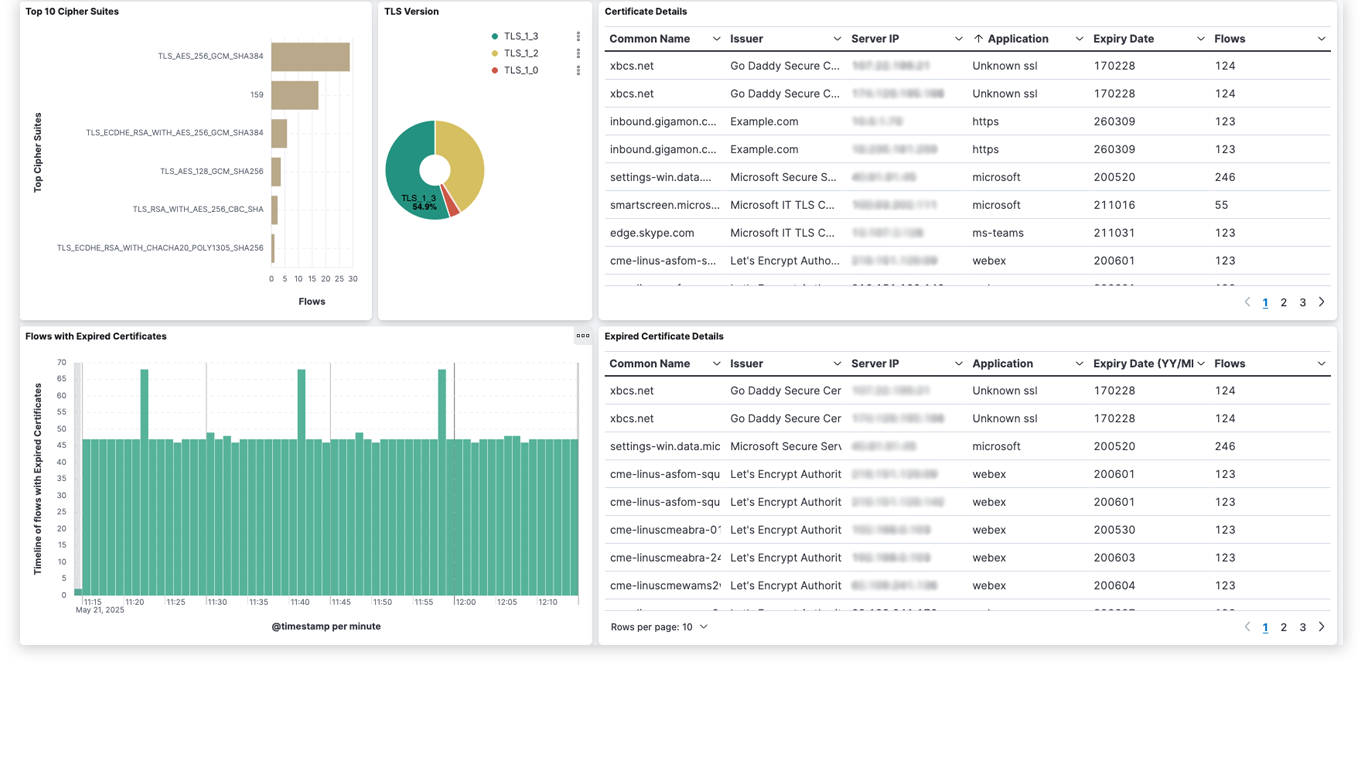
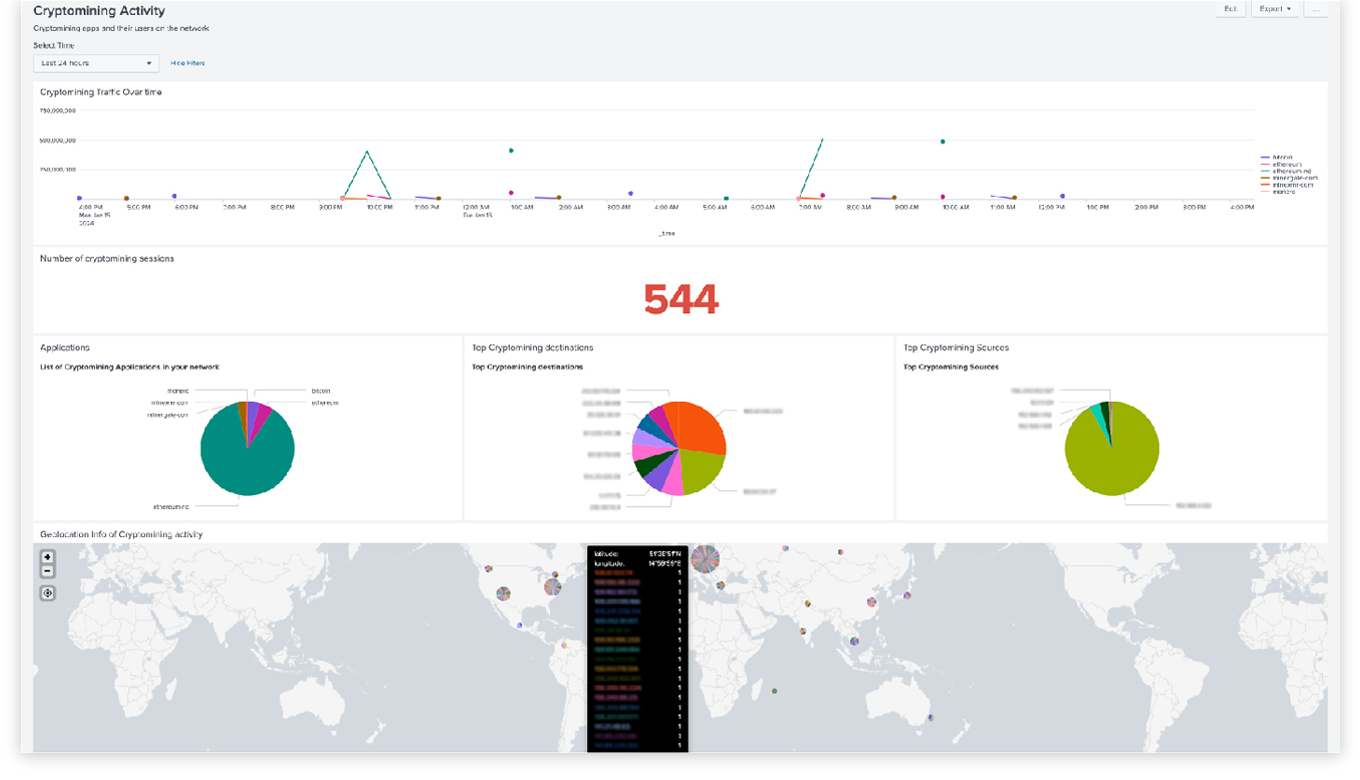
Dashboard View
Benefits
Derive Actionable Insights
Extract close to 6,000 app-related metadata elements from deep packet inspection to gain deeper context for improved performance and faster troubleshooting.
Boost Security Posture
Discover suspicious network activity, weak ciphers, expired TLS certificates, DNS tunneling, shadow AI usage, and rogue user activity such as crypto mining.
Enhance Situational Awareness
Augment logs with application metadata and business context for monitoring critical environments, workloads and microsegments.
Improve Application Performance and Network Security
Application Metadata Intelligence can be directly integrated and easily shared with observability and SIEM tools, internal IT systems, and other analytics tools, providing hard-to-find, specific application information to boost efficiency and effectiveness.
Product Details
Application Visualization
Uses deep packet inspection to identify over 4,000 applications and reveal usage patterns and network resource consumption through Application Metadata Intelligence and Application Filtering Intelligence
Application Metadata Exporter
Adds context to logs by converting AMI CEF records to JSON or OCSF for export via HTTPS/Kafka. Enrich user-plane data for mobile networks. Out of the box integrations with tools like Splunk, Dynatrace, MS Sentinel, and New Relic.
GigaVUE-FM
Get centralized deep observability orchestration and management. Configure traffic policies for VPC mirroring, UCT, and GigaVUE V Series with a simple drag-and-drop interface. Supports AWS and third-party orchestration methods, including Terraform.
“When we look for deep observability, Gigamon shows us everything we have in all layers of our infrastructure, including the cloud. We see the access network traffic, the packet, the flow, and so on— all the information that comes from our application metadata.”
"Gigamon AI Traffic Intelligence empowers security, compliance, and IT operations teams by revealing AI application traffic across hybrid and multi-cloud infrastructure."
“Application Metadata provides rich application data that helps enable IT to ‘triangulate’ performance bottlenecks and potential security vulnerabilities.”
Resources
Application Metadata Intelligence
Improve Hybrid Cloud Security and Performance
Application Intelligence
Frequently Asked Questions
Application Metadata Intelligence (AMI) expands upon the application layer visibility derived from Gigamon Application Visualization and Application Filtering Intelligence, and supports a comprehensive approach to obtain application behavior. AMI generates rich contextual information about your applications and protocols that you can send to your security and observability tools for analysis.
Application Metadata Intelligence is a crucial step in quickly identifying suspicious activities, performance bottlenecks and inefficiencies in your environment. Application Intelligence provides your business with a comprehensive view of application data within your network that will allow security and performance tools to do their jobs efficiently and accurately.
Application Metadata Intelligence is a crucial line of defense, as we see artificial intelligence (AI) accelerate breach rates and impact hybrid cloud security. To regain control of this new cloud security landscape, Gigamon leverages AI to enhance application visibility and network security. When paired with AI-driven security analytics tools, AI can automate detection and remediation processes using the actionable metadata provided by Gigamon AMI.
Application Metadata Intelligence and Application Filtering Intelligence are two of the ways Gigamon provides application intelligence to identify, filter, and enrich application data coming from your hybrid cloud. Application Filtering Intelligence (AFI) directs traffic by application or application family to the appropriate tools, to save storage and processing resources. On the other hand, Application Metadata Intelligence creates summarized and context-aware information about raw network packets, which helps your tools quickly spot suspicious activity and performance issues.
Gigamon uses deep packet inspection, which is a method of assessing the content of data packets in detail as they pass through the network, to extract insightful metadata from network traffic. This deeper inspection allows Gigamon to provide organizations with a granular understanding of the applications currently communicating in lateral traffic.
Application Metadata Intelligence (AMI) from Gigamon enhances application performance monitoring by extracting rich, real-time metadata from network traffic without relying on agents or payload decryption. This allows APM tools to identify bottlenecks, security risks, and performance issues much faster and provides consistent visibility across hybrid and multi-cloud environments. Gigamon also integrates seamlessly with top APM tools and observability tools to enrich insights while lowering data ingestion costs.
Application metadata can be a useful tool in detecting security threats by providing information and context about applications, users and system behaviors that is critical to assessing risk. Application Metadata Intelligence from Gigamon can be integrated into your existing infrastructure, so that this application metadata can be efficiently utilized to quickly identify performance bottlenecks, quality issues, and network security threats.
Dive Deeper